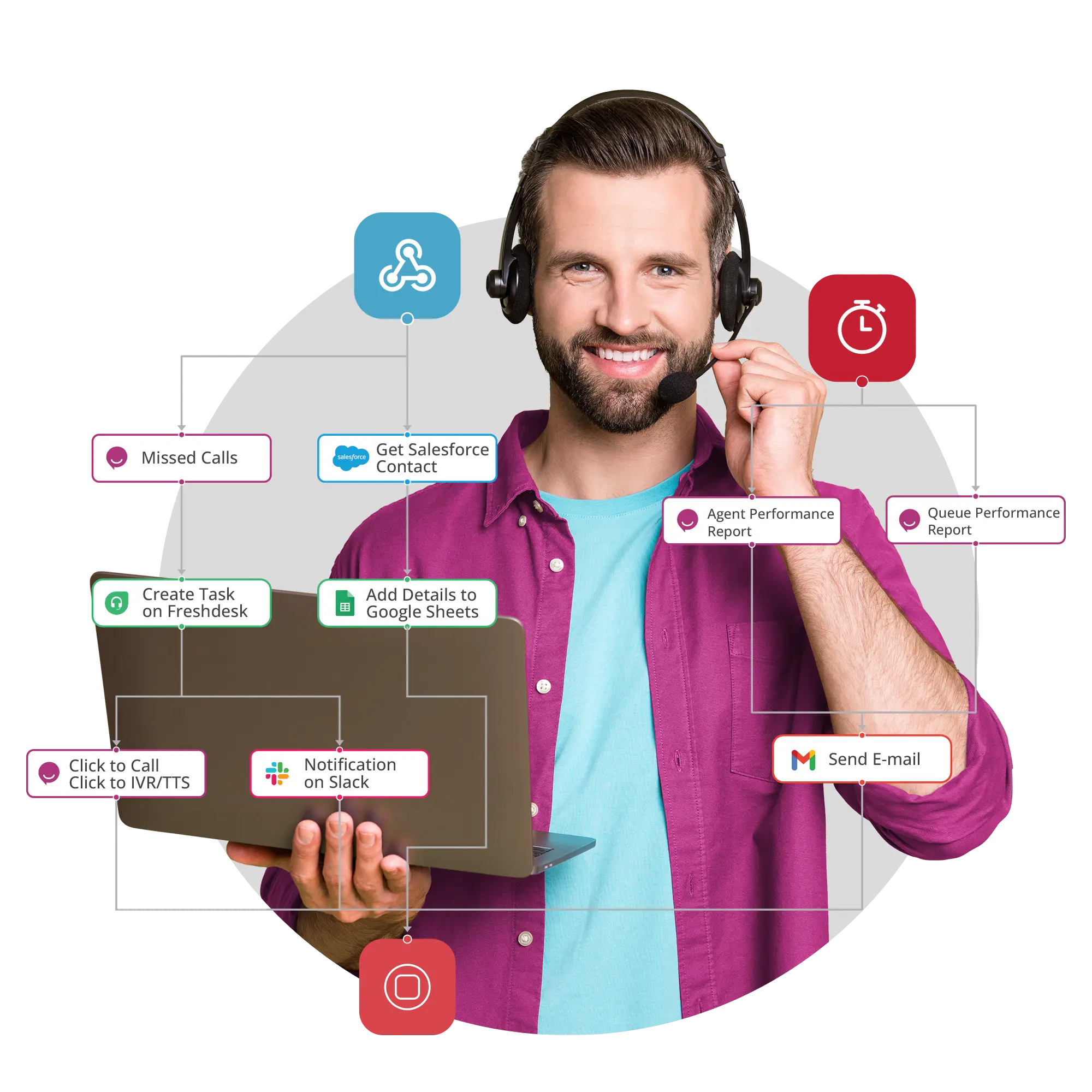
Quelles sont les considérations de sécurité essentielles pour la technologie des centres d'appel basés sur le cloud ?
Lesprincipaux aspects de la sécurité de la technologie decentre d'appels en nuage sont le cryptage des données, les contrôles d'accès, la conformité aux réglementations, l'assurance de la sécurité des fournisseurs, les mesures de sécurisation du réseau et les audits réguliers1. Ces actions empêchent la compromission des données des clients et garantissent un fonctionnement sécurisé.
Comprendre l'importance de la sécurité dans les centres d'appels basés sur le cloud
En comprenant la nature essentielle de la sécurité dans les centres d'appels basés sur le cloud, il devient évident que ces centres traitent des données confidentielles sur les clients, ce qui en fait des cibles privilégiées pour les cybermenaces2.
Les failles de sécurité peuvent entraîner des pertes financières coûteuses, des atteintes à la réputation et des actions légales. Par conséquent, de solides mesures de sécurité couvrant le cryptage, les contrôles d'accès, la conformité aux réglementations et des audits réguliers sont nécessaires pour assurer la sécurité des informations des clients et maintenir la confiance dans les services de centres d'appels basés sur le cloud.
Principales fonctionnalités de sécurité à rechercher
Parmi les principales fonctionnalités de sécurité à rechercher dans les solutions5 de centres d'appels basées sur le cloud figurent le cryptage pour la protection des données, les contrôles d'accès tels que l'authentification multifactorielle, la conformité aux réglementations sectorielles, les systèmes de détection/prévention des intrusions, les audits réguliers et les évaluations de la sécurité des fournisseurs. Ces caractéristiques permettent de défendre efficacement les données sensibles des clients et de se prémunir contre les cyberrisques futurs.
Cryptage et protection des données
Le cryptage et la protection des données jouent un rôle important dans la sécurité des solutions de centre d'appels basées sur le cloud. Le cryptage transforme les données sensibles des clients en un type sûr lors de la transmission et du stockage, ce qui empêche les personnes non autorisées d'y 3.
Ces contrôles protègent les données personnelles, les détails de paiement et les enregistrements d'appels contre l'interception et la divulgation accidentelle, garantissant ainsi la sécurité et la confidentialité des données des clients.
Contrôle d'accès et authentification
Le contrôle des appels et l'authentification sont les caractéristiques de sécurité de base des solutions de centre d'appels basées sur le cloud. Le contrôle d'accès permet aux administrateurs de définir les règles et les politiques de restriction d'accès aux données et aux ressources sensibles en fonction des rôles et des autorisations4 des utilisateurs.
Les systèmes d'authentification forte, y compris l'authentification multifactorielle, améliorent la sécurité en obligeant l'utilisateur à fournir plus d'une forme d'identification pour être autorisé à accéder au système. Ces contrôles contribuent à garantir l'accès non autorisé et la sécurité des informations sur les clients contre les menaces éventuelles.
Audits de sécurité réguliers et conformité
Des audits de sécurité et une conformité réguliers sont nécessaires pour préserver l'intégrité et la sécurité des solutions de centre d'appels basées sur le cloud.
Les audits de sécurité sont des évaluations méthodiques des contrôles et des processus de sécurité qui visent à détecter les vulnérabilités et les faiblesses, ce qui permet aux organisations de prévenir les failles de sécurité.
Le respect des réglementations sectorielles comme le règlement général sur la protection des données, garantit que les données sensibles des clients sont en sécurité et que les exigences légales sont respectées. Ces actions facilitent le maintien de la confiance des organisations envers les clients et la protection de la confidentialité et de l'intégrité des données des clients.
Défis liés à la sécurisation des centres d'appels basés sur le cloud
Les défis liés à la sécurisation des centres d'appels basés sur le cloud comprennent la protection des données sensibles des clients, la conformité aux exigences réglementaires, le contrôle d'accès, la sécurité du réseau, l'assurance de la sécurité des fournisseurs, les menaces internes et les plans6 d'intervention en cas d'atteinte à la protection des données.
Pour résoudre ces problèmes, une approche systématique doit comprendre des mesures de sécurité solides et une surveillance continue.
Menaces et vulnérabilités potentielles
Les menaces et les vulnérabilités liées aux centres d'appels basés sur le cloud comprennent les accès non autorisés, les violations de données, les attaques de phishing, les menaces d'initiés, les logiciels malveillants, les attaques par déni de service et les paramètres du cloud mal configurés7.
La dilution de ces menaces exige des mesures de sécurité solides, des évaluations de sécurité fréquentes et une formation continue du personnel afin de minimiser les menaces de manière holistique.
Équilibrer la convivialité et la sécurité
L'équilibre entre la convivialité et la sécurité dans les centres d'appels hébergés dans le cloud nécessite l'intégration d'une authentification conviviale, de contrôles d'accès, d'un cryptage, d'une formation complète et d'une surveillance continue. Ces contrôles facilitent l'efficacité des processus et protègent les données confidentielles contre d'éventuelles menaces.
Meilleures pratiques pour renforcer la sécurité
Les meilleures pratiques de sécurité dans les centres d'appels basés sur le cloud sont la mise en œuvre d'une authentification forte, d'un contrôle d'accès strict, du chiffrement des données sensibles, de mises à jour régulières du système, d'une évaluation de la sécurité, d'une formation du personnel, d'un système de détection des intrusions et d'un plan d'intervention en cas d'incident.
Toutes ces mesures contribuent à réduire les risques de sécurité et à empêcher l'accès non autorisé à des informations sensibles ou des violations du système.
Mettre en œuvre de solides politiques de protection des données
La mise en œuvre de politiques de protection des données solides est très importante pour protéger les informations sensibles dans les centres d'appels basés sur le cloud. Ces politiques détaillent les règles et les processus de traitement, de stockage et de transmission sécurisés des données afin de minimiser les accès non autorisés et les fuites de données.
En mettant en place des protocoles de cryptage solides, des contrôles d'accès et des audits de sécurité réguliers, les organisations peuvent garantir la conformité réglementaire et protéger les données des clients contre les menaces potentielles. En outre, la formation continue du personnel et les programmes de sensibilisation sont utilisés pour renforcer le principe de sécurité des données, en créant une culture de responsabilité et de vigilance au sein de l'organisation.
Former les employés aux protocoles de sécurité
La formation des employés aux protocoles de sécurité est nécessaire pour assurer la sécurité des données sensibles dans les centres d'appels basés sur le cloud. Cette formation apprend au personnel à identifier les menaces de sécurité, telles que les attaques de phishing ou les tentatives d'accès non autorisé, et à y répondre.
Les employés apprennent à traiter correctement les données des clients, à utiliser des méthodes d'authentification sûres et à suivre les politiques et procédures de l'entreprise en matière de gestion des risques. Des sessions de formation et des mises à jour régulières contribuent à la sensibilisation à la sécurité et permettent aux employés de participer activement à la garantie d'un environnement sécurisé.
L'investissement dans la formation des employés aide les centres d'appel à améliorer leur posture de sécurité en général et à réduire le risque d'incidents de sécurité.
Le rôle des fournisseurs dans la garantie de la sécurité
La sécurité des centres d'appels basés sur le cloud dépend en grande partie des fournisseurs. Ils sont chargés de déployer et d'appliquer des mesures de sécurité strictes destinées à protéger les données et l'infrastructure des clients.
Cela implique également l'installation de protocoles de cryptage, de contrôles d'accès et de systèmes de détection d'intrusion afin de se protéger contre les accès non autorisés et la perte de données. Les fournisseurs procèdent également à des évaluations et à des audits de sécurité réguliers afin de détecter et de corriger les éventuelles faiblesses de leurs systèmes8. En outre, ils s'assurent qu'ils respectent les réglementations et les normes du secteur, telles que le règlement général sur la protection des données, qui contribue à la protection de la vie privée des clients et à la sécurité des données.
Les fournisseurs se concentrent davantage sur la sécurité et offrent des détails clairs sur leurs procédures de sécurité, ce qui est la confiance dans leurs services, et par conséquent, un cadre sécurisé pour les opérations de centre d'appels basé sur le cloud est créé.
Choisir le bon logiciel de centre d'appels en nuage
Pour assurer le bon fonctionnement et la réalisation des objectifs de l'entreprise, il faut choisir un logiciel de centre d'appels cloud approprié. Lorsque vous choisissez une solution, pensez à des questions telles que l'évolutivité, la flexibilité, la facilité de mise en œuvre, l'ensemble des fonctionnalités, les capacités d'intégration, les fonctionnalités de sécurité et le coût. Cherchez une réponse qui satisfasse les besoins et les objectifs individuels de votre entreprise.
En outre, l'image du fournisseur et sa fiabilité doivent être prises en compte, de même que l'historique des services et de l'assistance fournis.
En analysant attentivement ces facteurs et en effectuant des recherches appropriées, vous pouvez sélectionner un logiciel de centre d'appels dans le cloud qui répond à vos exigences et contribue au succès de votre entreprise.
Comprendre les mesures de sécurité du fournisseur
Lors de la sélection d'une solution de centre d'appels basée sur le cloud, l'un des principaux éléments à prendre en compte est les mesures de sécurité du fournisseur. C'est le fournisseur qui doit mettre en œuvre et maintenir des protocoles de sécurité solides qui protègent les informations critiques des clients et garantissent la robustesse de ses systèmes.
Les principales mesures de sécurité à prendre en compte sont le cryptage des données, les contrôles d'accès, la détection des intrusions et les audits de sécurité périodiques. En outre, les fournisseurs devraient adhérer aux normes du secteur, telles que les réglementations générales sur la protection des données, et faire preuve de transparence en ce qui concerne leurs activités de sécurité.
Une évaluation approfondie des mesures de sécurité mises en place par le fournisseur permet à l'entreprise de prendre des décisions en connaissance de cause et de choisir une solution qui privilégie la sécurité des données et la sécurité opérationnelle.
Tendances futures de la sécurité des centres d'appels dans le cloud
L'avenir des tendances en matière de sécurité des centres d'appels dans le cloud comprendra probablement la détection avancée des menaces, l'automatisation et l'intégration de l'IA.
Cette évolution vise à promouvoir l'identification préemptive des menaces, à fluidifier et à améliorer le processus d'authentification, et à fournir des canaux de communication plus sûrs.
Progrès en matière de cryptage et de détection des menaces
Les améliorations dans le domaine du cryptage et de la détection des menaces apportent un partage significatif dans la sécurité du centre d'appels dans le cloud. L'amélioration des protocoles de cryptage garantit le secret et l'exactitude des données critiques en empêchant tout accès non autorisé.
D'autre part, les technologies avancées de détection des menaces s'appuient sur des algorithmes d'apprentissage automatique et d'intelligence artificielle pour détecter et prévenir les menaces de sécurité en amont, améliorant ainsi la posture de sécurité globale. Ces améliorations garantissent la sécurité des données des clients et préservent la foi dans les opérations des centres d'appels définies dans le cloud.
L'impact de l'IA et de l'apprentissage automatique sur la sécurité
L'IA et l'apprentissage automatique ont transformé la sécurité des centres d'appels basés sur le cloud, grâce à la détection proactive des menaces, à la réponse rapide aux menaces et à l'authentification supérieure.
Ces technologies analysent les données pour trouver des modèles et des anomalies, ce qui aide à reconnaître les risques de sécurité probables avant qu'ils ne deviennent sérieux.
En outre, les techniques d'authentification infusées par l'IA, c'est-à-dire la reconnaissance bio-métrique entre autres, améliorent la sécurité et le confort de l'utilisateur.
Références bibliographiques
1 - La sécurité dans les centres d'appels basés sur le cloud :
¹ Sharma, S., & Sood, S. K. (2018). Défis en matière de sécurité et de confidentialité dans l'informatique en nuage : A Survey. Informatique appliquée et informatique, 14(1), 59-79.
² Gruschka, N., & Jensen, M. (2010). Attack Surfaces : A Taxonomy for Attacks on Cloud Services (Une taxonomie pour les attaques sur les services cloud). Actes de la conférence internationale de l'IEEE sur le cloud computing, 276-279.
2 - Cryptage et protection des données :
Ristenpart, T., Tromer, E., Shacham, H. et Savage, S. (2009). Hey, You, Get Off of My Cloud : Exploring Information Leakage in Third-Party Compute Clouds. Proceedings of the 16th ACM Conference on Computer and Communications Security, 199-212.
⁴ Chen, D. et Zhao, H. (2012). Questions relatives à la sécurité des données et à la protection de la vie privée dans l'informatique en nuage. 2012 International Conference on Computer Science and Electronics Engineering, 647-651.
3 - Contrôle d'accès et authentification :
⁵ Zissis, D., & Lekkas, D. (2012). Traiter les problèmes de sécurité de l'informatique en nuage. Future Generation Computer Systems, 28(3), 583-592.
⁶ N IST. (2013). Directive sur l'authentification électronique. Institut national des normes et de la technologie, publication spéciale 800-63-2.
4 - Audits de sécurité réguliers et mise en conformité :
⁷ Leavitt, N. (2010). L'informatique en nuage est-elle vraiment prête pour le prime time ? Computer, 43(1), 15-20.
⁸ Jansen, W., & Grance, T. (2011). Lignes directrices sur la sécurité et la confidentialité dans l'informatique en nuage publique. National Institute of Standards and Technology, Special Publication 800-144.